As what is the primary objective of data security controls takes center stage, this opening passage beckons readers into a world crafted with authoritative knowledge, ensuring a reading experience that is both absorbing and distinctly original. Data security controls play a pivotal role in safeguarding sensitive information, and understanding their primary objective is crucial for effective data protection.
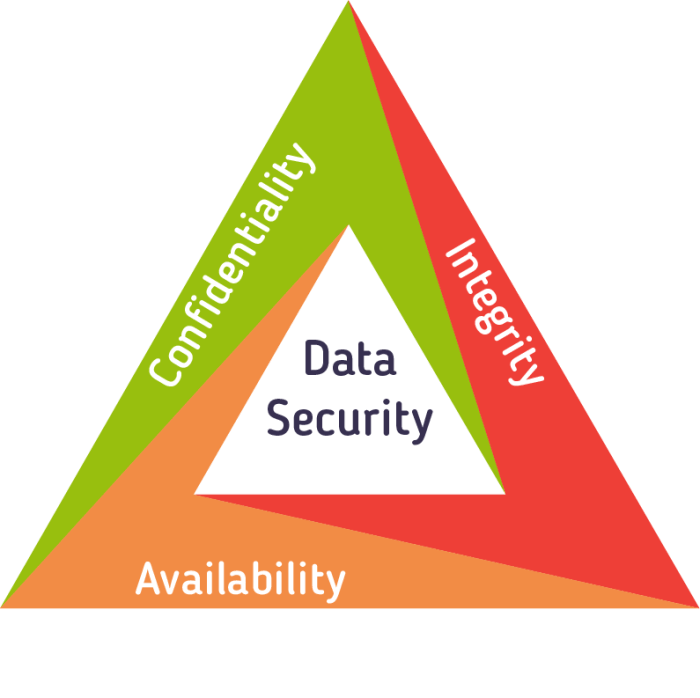
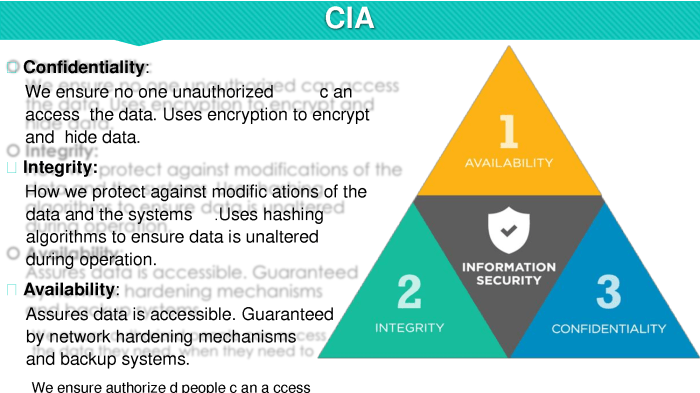
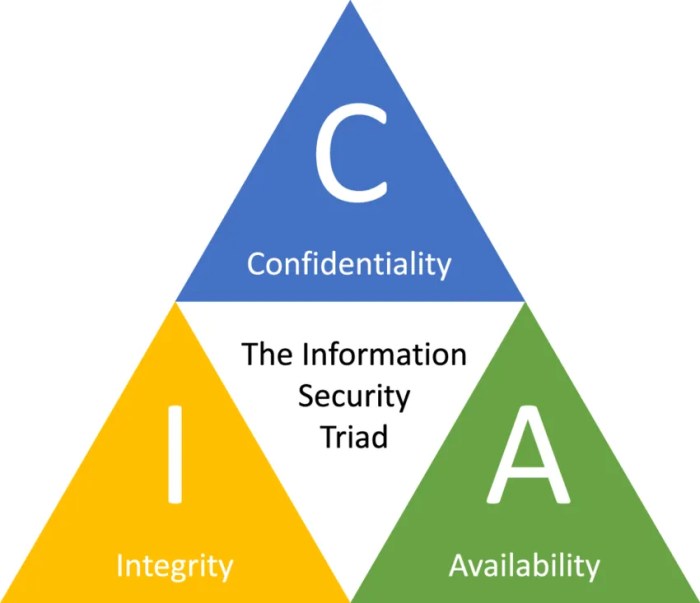
Data security controls are a comprehensive set of measures designed to protect data from unauthorized access, use, disclosure, disruption, modification, or destruction. Their primary objective is to ensure the confidentiality, integrity, and availability of data, known as the CIA triad.
Confidentiality refers to protecting data from unauthorized access, ensuring that only authorized individuals can view or use it. Integrity pertains to maintaining the accuracy and completeness of data, preventing unauthorized alterations or corruptions. Availability ensures that data is accessible to authorized users when needed, without disruptions or delays.
Data Security Controls: Definition and Purpose
Data security controls are measures or processes implemented to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. They play a crucial role in safeguarding data confidentiality, integrity, and availability, ensuring that it remains secure and accessible to authorized users only.
The primary objective of data security controls is to prevent, detect, and mitigate threats to data security. By implementing appropriate controls, organizations can reduce the risk of data breaches, data loss, and other security incidents that could compromise the integrity and confidentiality of their data.
Examples of Common Data Security Controls
- Access controls: Restricting who can access data based on their role and authorization level.
- Encryption: Encrypting data at rest and in transit to protect it from unauthorized access.
- Data masking: Redacting or obscuring sensitive data to protect it from unauthorized disclosure.
- Intrusion detection and prevention systems: Monitoring networks and systems for suspicious activity and preventing unauthorized access.
- Firewalls: Blocking unauthorized access to networks and systems.
Types of Data Security Controls: What Is The Primary Objective Of Data Security Controls
Data security controls can be classified into three main types:
Physical Controls, What is the primary objective of data security controls
Physical controls are tangible measures that protect data from physical threats, such as unauthorized access to physical locations or devices.
- Access control systems: Controlling physical access to data centers, servers, and other sensitive areas.
- Surveillance systems: Monitoring physical locations to detect unauthorized access or activity.
- Environmental controls: Maintaining proper temperature, humidity, and other environmental conditions to protect data from damage.
Technical Controls
Technical controls are software and hardware-based measures that protect data from logical threats, such as unauthorized access or data breaches.
- Firewalls: Blocking unauthorized access to networks and systems.
- Intrusion detection and prevention systems: Monitoring networks and systems for suspicious activity and preventing unauthorized access.
- Encryption: Encrypting data at rest and in transit to protect it from unauthorized access.
Administrative Controls
Administrative controls are policies, procedures, and guidelines that govern the use and protection of data.
- Data security policies: Defining the rules and regulations for data handling, access, and protection.
- Data classification: Classifying data based on its sensitivity and criticality.
- User training: Educating users on data security best practices and their responsibilities in protecting data.
Question & Answer Hub
What are the different types of data security controls?
Data security controls can be categorized into three main types: physical, technical, and administrative. Physical controls include physical barriers, access control systems, and environmental controls. Technical controls involve encryption, firewalls, intrusion detection systems, and data backup systems. Administrative controls encompass policies, procedures, and training programs that govern the handling and protection of data.
How do I implement data security controls effectively?
Effective implementation of data security controls requires a comprehensive approach that involves risk assessment, risk management, and best practices. Risk assessment helps identify potential threats and vulnerabilities, while risk management determines appropriate controls to mitigate those risks. Best practices include using strong passwords, implementing multi-factor authentication, and regularly patching software and systems.
What are the benefits of data security controls?
Data security controls provide numerous benefits, including protection against data breaches, compliance with regulations, improved data quality, enhanced customer trust, and reduced operational risks. By implementing effective controls, organizations can safeguard their sensitive information, maintain its integrity, and ensure its availability.